Some part of TAC’s architecture is still under development and in roadmap.
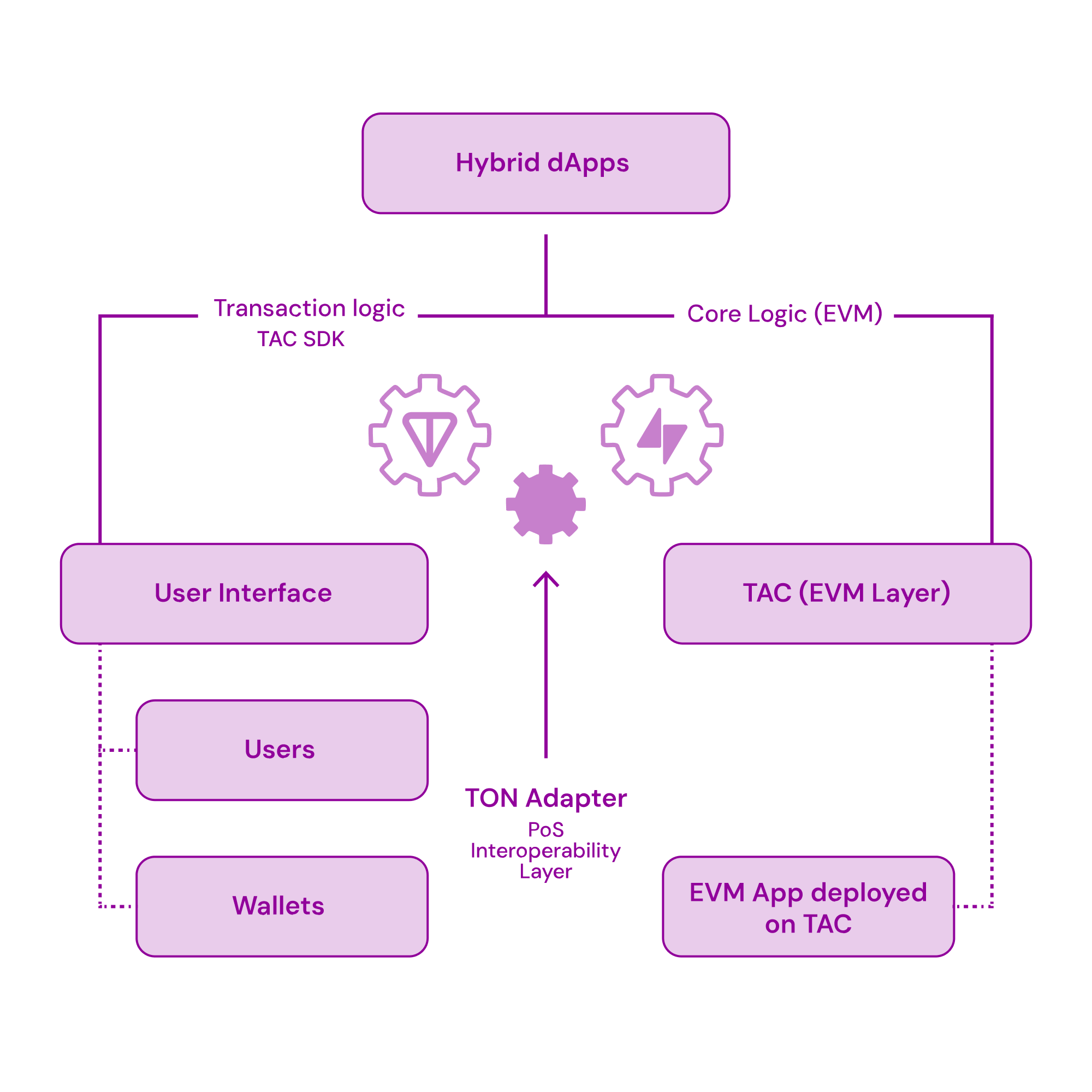
Architecture Overview
TAC EVM Layer
Full EVM compatibility with Cosmos SDK. Handles all application logic and state.
TON Adapter
Distributed sequencer network that securely routes messages between TON and
EVM.
Proxy Contracts
Smart contracts that translate between TON and EVM, making apps feel native to both sides.
TAC EVM Layer
The foundation of TAC is a complete Layer 1 blockchain that provides full EVM compatibility without compromises.TON Adapter Network
The TON Adapter is a purpose-built messaging system that securely connects TON and TAC EVM. Unlike traditional bridges, it’s designed specifically for application-level interactions.Current Network Status: The sequencer network is currently distributed but
not decentralized. Full decentralization is on the roadmap as the network
matures.
Core Functions
The TON Adapter handles five critical operations:Message Operations
- Transaction execution coordination
- Cross-chain calls
- Return value routing
Consensus Operations
- Merkle tree formation
- Multi-group validation
- Economic security enforcement
Sequencer Network Architecture
Individual Sequencers
Each sequencer monitors both TON and TAC EVM for relevant events,
maintaining local databases of transactions and forming initial Merkle
trees.
Sequencer Groups
Sequencers organize into groups that must reach 3/5 internal consensus. Each
group validates transactions independently and stakes collateral as security.
Network Consensus
Multiple groups must submit identical Merkle trees to achieve network-wide
consensus. This creates multiple validation layers for maximum security.
Economic Security
Stake Requirements
Stake Requirements
Every sequencer group must stake collateral:
- Minimum stake set by DAO governance
- Higher stakes earn proportionally higher rewards
- Stake must remain above threshold during participation
- Partial stake locking during proof submission
Reward Distribution
Reward Distribution
Performance-based incentives:
- Rewards distributed proportionally to stake size
- Executor selection based on collateral weight
- Commission sharing within groups
- Penalty mechanisms for incorrect operations
Governance & Elections
Governance & Elections
Democratic group selection:
- New groups approved through DAO voting
- Regular election cycles (DAO configurable)
- Performance monitoring and rating systems
- Penalty applications and network-wide voting
Proxy Contract System
Proxy contracts are the interface layer that makes cross-chain interaction feel seamless. They handle all the complexity of message formatting, asset management, and protocol translation.How Proxies Work
- TON Side
- EVM Side
Handled automatically by TAC SDK: When a user initiates a transaction using their TON wallet, the TAC SDK takes care of formatting the request for cross-chain delivery. The user’s assets are securely locked within the TON Adapter, and throughout the process, the SDK continuously monitors and reports the transaction status. This seamless integration ensures that users and developers do not need to manage the complexities of cross-chain communication themselves.
Developers don’t need to write TON-side proxy contracts - the TAC SDK
handles everything
Proxy Generation
Automatic Proxy Creation
Automatic Proxy Creation
TAC can automatically generate proxy contracts for many common use cases:
- Token transfers and swaps
- Liquidity provision and removal
- Standard DeFi interactions
Custom Proxy Development
Custom Proxy Development
For complex applications, developers can create custom proxies:
- Handle application-specific logic
- Implement custom validation rules
- Manage complex state transitions
- Integrate with multiple contracts
Complete Transaction Lifecycle
Here’s how all three layers work together for a complete cross-chain transaction:Initiation (TON)
User action triggers the process:
- User connects TON wallet to hybrid dApp
- Selects action (swap, stake, etc.) and confirms transaction
- TON-side proxy locks assets and creates formatted message
Detection (TON Adapter)
Sequencers monitor and collect:
- Sequencers detect new events on TON
- Transaction details stored in local databases
- Asset transfers validated against message parameters
Consensus (TON Adapter)
Multi-layer validation process:
- Individual sequencers form Merkle trees
- Groups reach 3/5 internal consensus (BFT threshold)
- Cross-group validation ensures network agreement
- Cryptographic proofs generated for execution
Execution (TAC EVM)
Target chain processes transaction:
- EVM proxy receives validated message
- Assets are minted or unlocked as needed
- Target contract methods executed with parameters
- Results and state changes recorded on-chain
Security Guarantees
TAC’s architecture provides multiple layers of security across all components:Message Security
- Merkle proofs validate transaction inclusion
- Multiple signature requirements prevent fraud
- Asset validation ensures accurate transfers
- Rollback protection for failed transactions

